 KASPERSKY ENDPOINT SECURITY
KASPERSKY ENDPOINT SECURITY
FOR ENTERPRISE
Next-generation protection against advanced threats targeting your endpoints and users
POWERFUL SECURITY
POWERFUL PERFORMANCE
POWERFUL THREAT INTELLIGENCE
CENTRALIZED MANAGEMENT
Multi-layered Protection
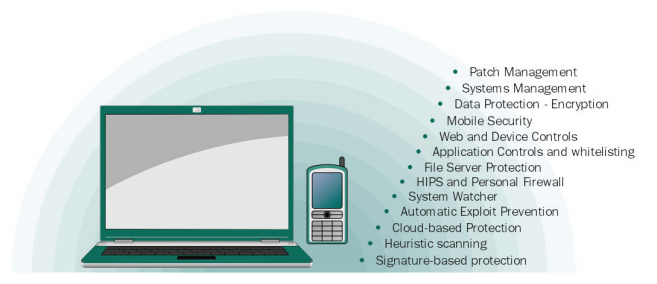
Unequalled Next-Generation Threat Preventionand Elimination
• Multi-Algorithm Heuristic Analysis – detects unknown malware, supplementing traditional signaturebased technologies.
• Cloud-Assisted Kaspersky Security Network (KSN) – facilitates the identifi cation and blocking of new malware threats in real time as they emerge.
• Automatic Exploit Prevention – helps proactively stop even the most advanced threats through blocking exploits used by cybercriminals.
• System Watcher — Blocks unknown threats by detecting suspicious behaviour patterns, and restores key fi les should the system be impacted
• Host-based Intrusion Prevention System (HIPS) — restricts activities and grants privileges according to the software’s trust level
• Personal Firewall restricts network activity
• Network Attack Blocker stops network-based attacks
• File servers are also fully protected
Every Endpoint Under Your Control
- LOWER YOUR EXPOSURE TO ATTACK VIA APPLICATIONS – Dynamic Whitelisting, Application Control
- CLOUD-EMPOWERED FLEXIBLE WHITELISTING
- ADDRESSING THE DANGERS OF WEB BROWSING -Web Control
- CONTROLLING THE USE OF PORTABLE DEVICES – Device Control
Protecting Data Through Integrated Encryption
Eliminating Vulnerabilities Through Intelligent Patching
Securing Mobile Endpoints Beyond Your Perimeter
• Powerful multi-layered protection against malware threats for all leading mobile platforms.
• Anti-phishing technology – blocks dangerous links in messages and web pages while calls/sms fi lters
prevents unwanted communication
• Application wrapping – allows corporate data to be containerized, encrypted and wiped separately
on employee owned devices.
• Application control and web control supported by KSN, blocking unauthorized software and website access.
• Anti-theft – features including wipe, device lock, locate, SIM watch, ‘mugshot’ and ‘alarm’ device detection allowing the swift disablement of devices and erasure of any sensitive data when a device is lost or stolen.
• Jailbroken or rooted device detection and reporting, so action can be taken.
• Centralized management – including Mobile Device and Applications Management. (MDM/MAM)
functionality. Policies can be deployed to heterogeneous devices on all major platforms from a single
interface.
Optimised Efficiency – Integrated Management
For more information : sales@myberry.co.th
